TLS version update
Transport Layer Security is a cryptographic protocol that ensures secure communication over a network. In the context of Azure Cloud, TLS is used to establish a secure connection between clients and Azure services, providing encryption, data integrity, and authentication. This helps protect sensitive data and communications transmitted between Azure-based applications, resources, and users, safeguarding them from unauthorised access and potential security threats. By implementing TLS, Azure Cloud ensures that data exchanged within its environment is kept confidential and secure.
Microsoft and other leading cloud providers are disabling TLS 1.0 and 1.1 due to security concerns and the need to maintain a secure and robust communication environment. TLS 1.0 and 1.1 are older versions of the TLS protocol that have known security vulnerabilities and weaknesses. As a result, Microsoft is phasing out support for these outdated versions to prioritise the use of more secure and modern cryptographic protocols, such as TLS 1.2 and later versions. This proactive approach helps protect users and organisations from potential security risks associated with the use of obsolete and vulnerable encryption protocols, ensuring a higher level of data security and integrity within the Azure Cloud environment.
To provide best-in-class encryption for your data and to minimise the security risk, we'll require interactions with our services to be secured using TLS 1.2 or later from April 2024, when support for TLS 1.0 and 1.1 will end.
How to check if you're TLS 1.2 compliant
Utilise a platform for testing and debugging APIs, making HTTP requests, and inspecting server responses. Examples of such platforms include Postman, SoapUI, RESTClient, Katalon Studio, etc.
Within the platform, configure specific TLS versions for requests.
- In the request settings, look for an option to configure TLS settings or security settings.
- Select the specific TLS version that you want to use for requests
- Run a request in our test environment for example (GET, POST, PULL, etc); and
- Inspect the server responses
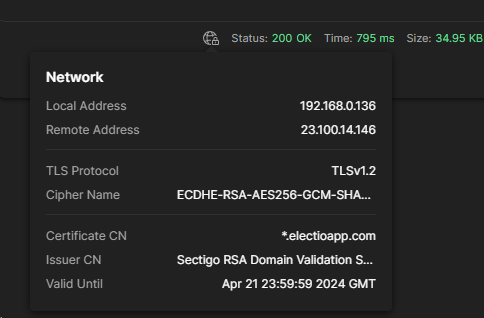
How to check your systems for TLS configurations
To identify TLS and cipher settings in cloud environments, the providers offer tools and services that allow you to monitor and manage these configurations.
Azure
You can identify TLS and cipher settings using the following methods:
- Azure Security Center: You can use Azure Security Center to assess the security state of your Azure resources, including identifying TLS and cipher configurations.
- Azure Monitor: Azure Monitor can be used to collect and analyse telemetry data from your Azure resources, including data related to TLS and cipher configurations.
Amazon Web Services
In AWS, you can identify TLS and cipher settings using the following methods:
- AWS Config: AWS Config provides a detailed view of the configuration of AWS resources, including identifying TLS and cipher configurations.
- AWS CloudTrail: AWS CloudTrail can be used to capture API calls made in your AWS account, which can help in identifying changes to TLS and cipher settings.
Manual identification methods
We can also identify manually using the following methods:
Connect to your VM via SSH
Connect to access the VMs hosted on Azure and visually review the TLS settings and cipher configurations within the operating system's network and security settings.
- Registry Inspection: Access the registry editor on the VMs and navigate to the TLS and cipher suite configurations to manually inspect and verify the enabled protocols and ciphers.
- Windows:
Examine registry keys underHKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration\Local\SSL\00010002for TLS protocols and cipher suites. - Linux:
Check configuration files in/etc/ssl,/etc/httpd/conf.d/or/usr/local/sslfor TLS protocols and cipher suites.
- Windows:
Command Line Tools
Utilise command line tools such as PowerShell or Command Prompt to run commands that retrieve information about the TLS protocol versions and cipher suites enabled on the VMs.
- PowerShell command Get-TlsCipherSuite on a Windows server to list all cipher suites
- Run openssl ciphers -v to list available ciphers.
- Connect to a specific website or service with
openssl s_client -connect <hostname>:<port>and examine the output for TLS version and cipher details.
Network Packet Analysis
Use network packet analysis tools to capture and analyse network traffic to and from the VMs, allowing you to observe the TLS handshake details and cipher suite negotiations.
Nmap
- Use nmap --script ssl-enum-ciphers -p
to scan specific ports and list supported ciphers. - Wireshark:
- Use Wireshark to capture and analyse network traffic
- Tcpdump: is primarily designed for Unix-like operating systems.
To capture packets to file:tcpdump -i eth0 -w capture.pcap- Open the file in Wireshark analyse the connections bring Server and clients
Browser tools
Use tools such as SSL Server Test which can bring up all the information about your server including TLS protocols and cipher suites.
Open SSL Server Test (Powered by Qualys SSL Labs) add your hostname and scan for results.
Before making any changes, it is best practice to backup any config.
Here is an example of a high-level test plan:
- Run a scan on the host
- Take a record of the results
- Backup the configuration
- Apply the TLS and cipher changes
- Run network packet analysis
- Run regression pack + Integration tests
- Monitor logs and network packet analysis
If you have any questions regarding our TLS ciphers, please contact Sorted Customer Support at support@sorted.com.